Get Your SSL Cert via acme.sh
Install acme.sh
Install the script of acme.sh.
curl https://get.acme.sh | shThen reload your shell.
For example:
source ~/.bashrcCreate Cloudflare API Key
I strongly recommend DNS API mode for this, if this domain is not a free domain from freenom.com.
First of all, add your domain to Cloudflare. I won’t show how to do this just because it’s way too simple.
…
Create an API token so that acme.sh can use it.
Do not hand in your global API key so simply.
Remember to copy the Zone ID and Account ID shown above.
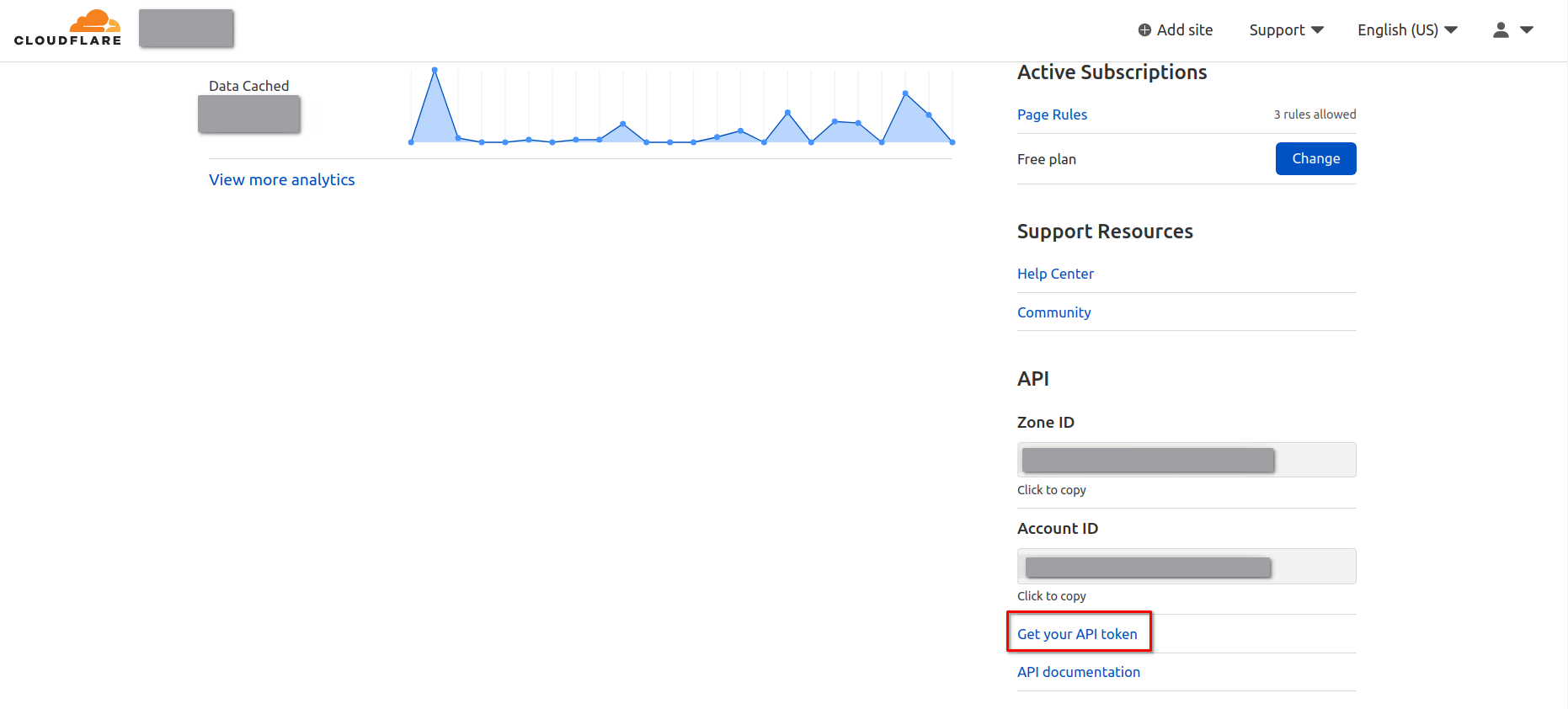
Click “Create Token”.
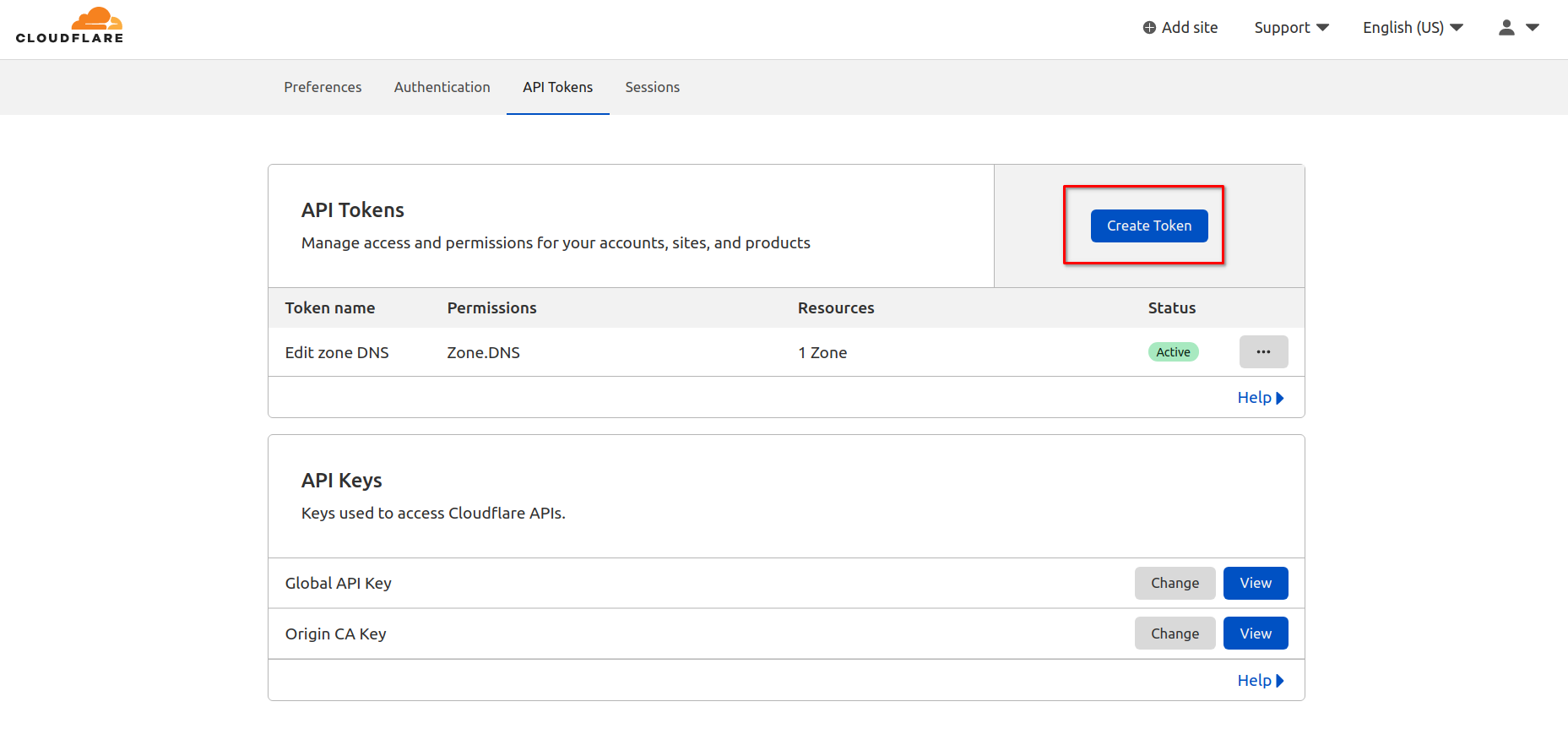
Cloudflare provides a template for that, just use it.
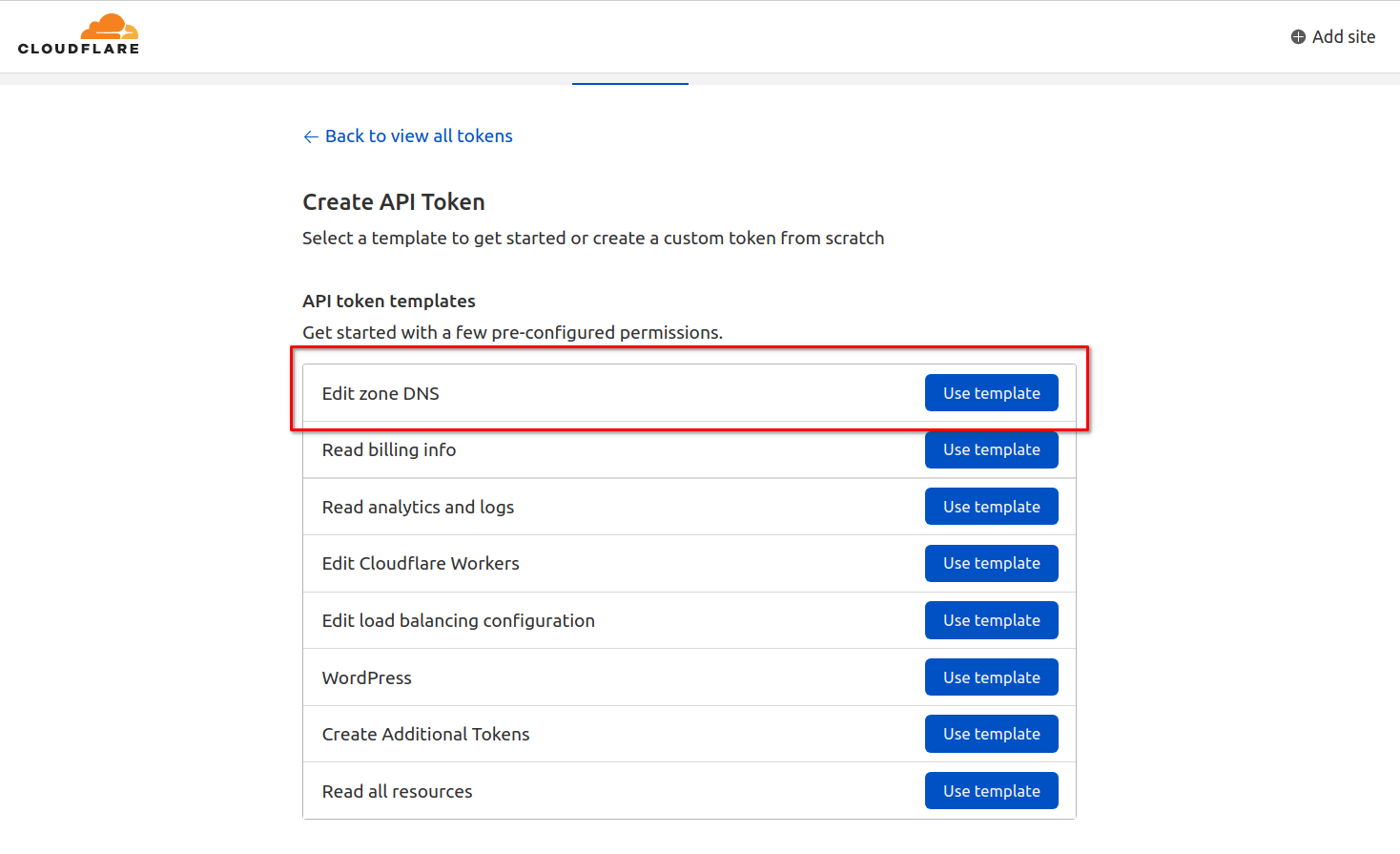
Choose the specific zone.
Add TTL as you like.
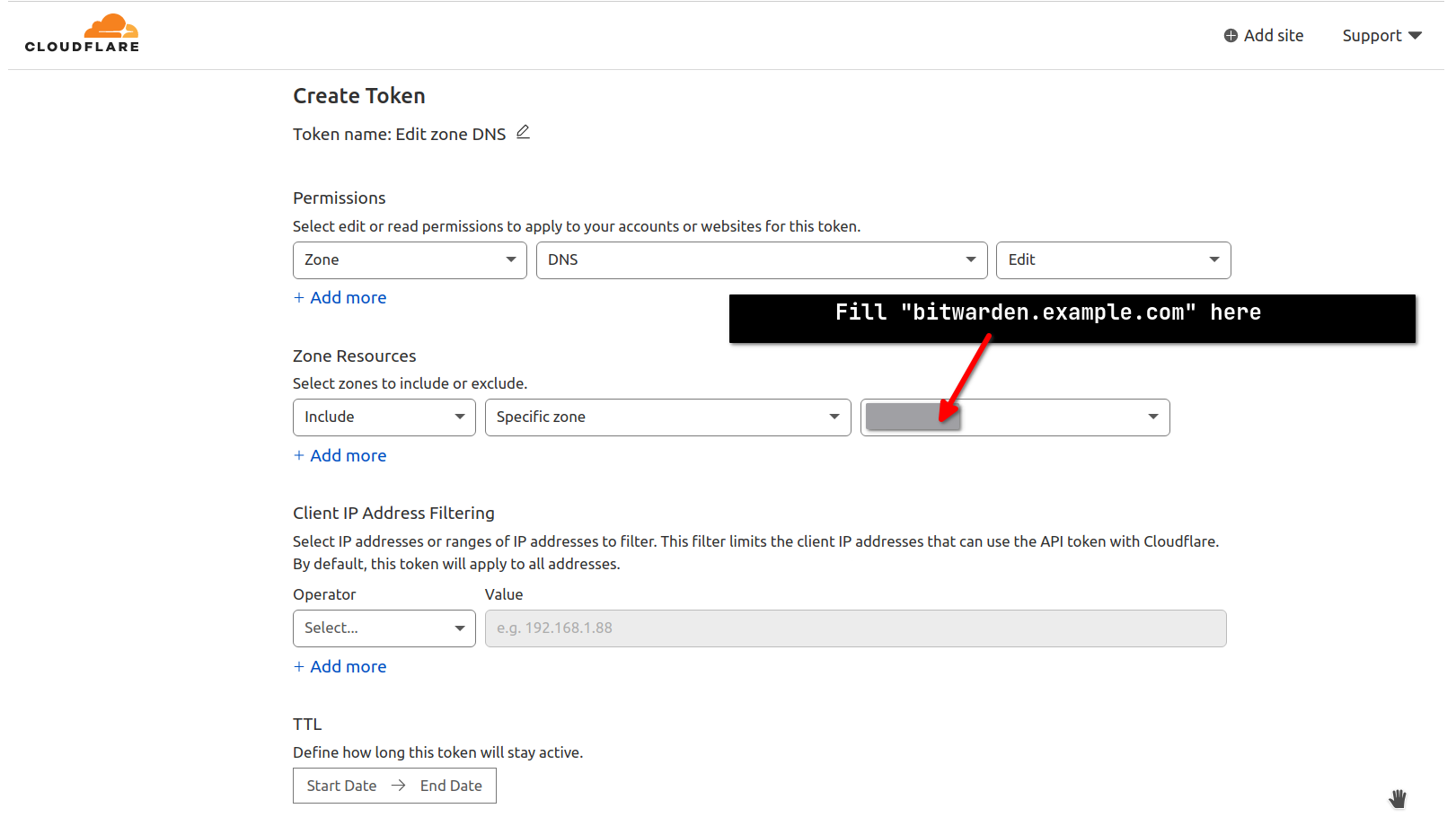
Confirm the settings of the token.
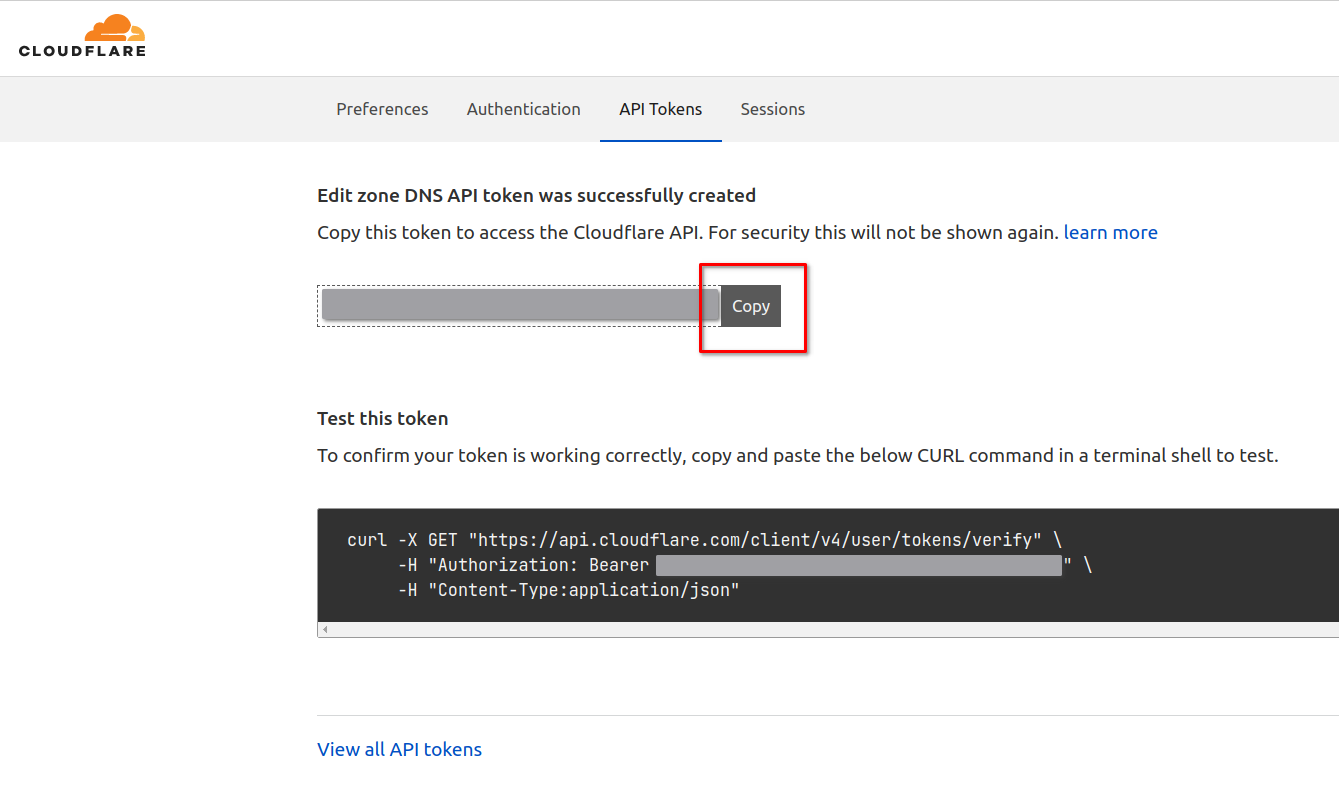
Copy the token and test it.
Must copy! This token will never be displayed again once you leave this page.
Time to Use acme.sh
Register the fxxxing zerossl account.
acme.sh --register-account -m my@example.comThen add environment variables for acme.sh
export CF_Token='xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
export CF_Account_ID='xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
export CF_Zone_ID='xxxxxxxxxxxxxxxxxxxxxx'Then simply start a request and acme.sh will do everything automatically.
Using an ECC cert is good. Add --force as your need.
acme.sh --issue -d example.com --dns dns_cf --keylength ec-256 Then you could see where the cert and keys are stored.
The script will set up a cron task, trying to renew the cert using the API when it is about to expire.
Fxxx ZeroSSL
The default CA provider has been switched to ZeroSSL from Let’s Encrypt.
But I have frequently come into very slow response from the poor service of ZeroSSL, I decided to switch back.
A parameter --server is needed to specify the CA server. As for let’s encrypt, it could look like this:
acme.sh --server letsencrypt --issue -d example.com --dns dns_cf --keylength ec-256 DNS manual mode
This mode does not need a A or AAAA record.
Add --force as your need.
acme.sh --issue -d example.com --dns --keylength ec-256 --yes-I-know-dns-manual-mode-enough-go-ahead-please The output should look like this:
Add the following TXT record:
Domain: '_acme-challenge.example.com'
TXT value: 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx'
Please be aware that you prepend _acme-challenge. before your domain
so the resulting subdomain will be: _acme-challenge.example.com
Please add the TXT records to the domains, and re-run with --renew.
Please add '--debug' or '--log' to check more details.
See: https://github.com/acmesh-official/acme.sh/wiki/How-to-debug-acme.shAdd TXT record as the instruction presented. Check it before continue.
dig txt _acme-challenge.example.comThen renew the cert.
acme.sh --renew -d example.com --dns --ecc --yes-I-know-dns-manual-mode-enough-go-ahead-pleaseThe cert will expire in 90 days. Remember to renew it in time.
Custom working directory
The script supports custom working directory. This is very useful when you want it to work somewhere else, making it possible to run several different profiles at the same time.
Type acme.sh --help and you can find:
--home <directory> Specifies the home dir for acme.sh
...
--config-home <directory> Specifies the home dir to save all the configurations.All you have to do is to append these two parameters in the front of the command.
And this won’t create an automatic cron job for auto renew, it has to be done manually.
Add the line below to your cron config:
59 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" --config-home /root/myacmeconfig/ > /dev/null